· Alex · security
How Many Keys Are Used in Symmetric Cryptography?
Applications, types of ciphers, pros and cons, key management, storage, integration with other cryptographic primitives and vulnerabilities

Applications, types of ciphers, pros and cons, key management, storage, integration with other cryptographic primitives and vulnerabilities

General ways of reporting malicious actors to social media providers, gaming platforms and law enforcement

How to get into ethical hacking, motivation, mindset, essential skills, pathways, legal aspects

A dive into the top web application vulnerabilities, including injection flaws, XSS, authentication and session management issues, XXE, CSRF, insecure deserialization, and more
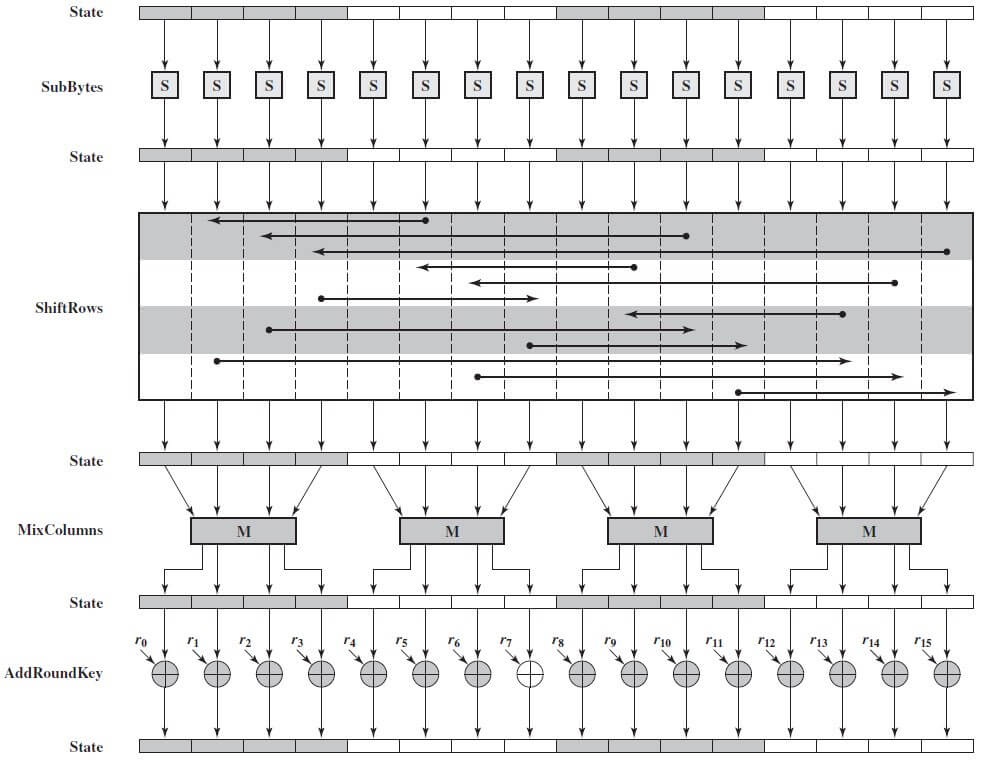
How AES works and how it applies to application security
The 4 phases of the OWASPs Testing Guide and key testing techniques